In an increasingly digital world, understanding different types of cyber security systems is vital for protecting sensitive information and ensuring online safety. These systems play a crucial role in defending against ever-evolving cyber threats that can disrupt personal lives and businesses alike. Familiarity with various security systems helps individuals and organizations select the best solutions to safeguard their digital assets.
Network Security
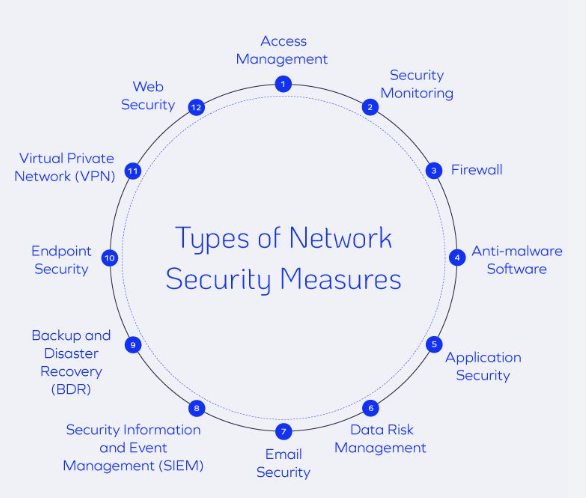
Network security focuses on protecting the integrity and usability of networks and data. It involves implementing measures to monitor and control access to the network, thereby preventing unauthorized intrusions and data breaches. Firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) are common tools used in network security to create a robust defense against external threats.
Application Security
Application security involves measures taken to enhance the security of software applications throughout their development lifecycle. This includes practices such as secure coding, regular vulnerability assessments, and application testing. By addressing potential weaknesses early in development, organizations can shield their applications from attacks like SQL injection and cross-site scripting, ultimately protecting their data and users.
Endpoint Security
Endpoint security focuses on securing end-user devices such as computers, laptops, and mobile devices that connect to the network. With the rise of remote work and bring-your-own-device (BYOD) policies, endpoint security has become increasingly critical. It includes antivirus software, endpoint detection and response (EDR) tools, and mobile device management (MDM) solutions to safeguard devices from malware and cyber threats.
As cyber threats continue to evolve, staying informed about different cyber security systems is essential for everyone. Whether you’re an individual user or part of a business, understanding these systems can help you make informed decisions about protecting your digital environment. Encourage yourself to dive deeper into the topic and explore more strategies to enhance your cybersecurity measures!