Communication technology plays a crucial role in how we interact and share information in today’s fast-paced digital world. Understanding authentication mechanisms is essential for safeguarding data and personal privacy, especially as cyber threats continue to evolve. This knowledge empowers individuals and organizations to implement effective security measures, ensuring information integrity and confidentiality.
Understanding Communication Technology
At its core, communication technology refers to the tools and platforms that facilitate the exchange of information. This includes everything from emails and instant messaging to video conferencing and social media. As these technologies advance, they enable seamless connectivity, promoting collaboration across distances. However, this rapid evolution also brings challenges, particularly concerning data security and user privacy.
Authentication Mechanisms Explained
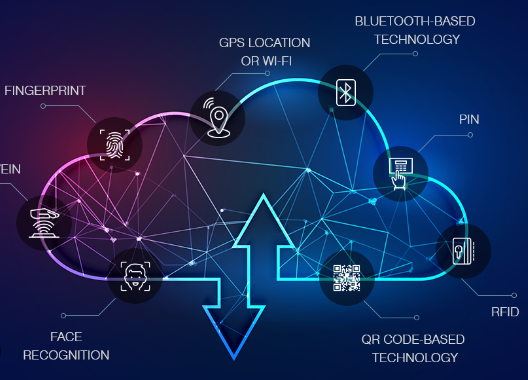
Authentication mechanisms are protocols that verify the identity of users before granting access to systems or data. These can range from simple password protection to more complex methods like multi-factor authentication (MFA), which may involve biometric data, such as fingerprints or facial recognition. By implementing robust authentication mechanisms, organizations can mitigate unauthorized access, protecting sensitive information from cyber threats.
The Importance of Security in Communication
In a world where data breaches are increasingly common, ensuring secure communication is paramount. Weak authentication practices can lead to substantial financial losses and damage to reputation. Individuals and organizations must prioritize security by adopting best practices, such as regularly updating passwords and employing multi-factor authentication, to create a safer digital environment. Educating all users about the importance of these measures is crucial for maintaining privacy and data integrity.
In conclusion, as communication technology continues to evolve, so too must our understanding of authentication mechanisms. Take proactive steps to secure your digital interactions by learning more about these essential tools and their applications. Empower yourself with knowledge and ensure your data remains protected.